Chalmers ambition är att bli en av Europas främsta akademiska miljöer 2041 och därmed bidra i ännu högre grad till Sveriges konkurrenskraft och omställningen mot ett hållbart samhälle. Vår forskning spänner över 13 institutioner, omsätter närmare 3 miljarder kronor och publiceras i cirka 3 000 vetenskapliga artiklar årligen.
Forskingsområden i urval
Dessa forskningsområden spänner över flera institutioner och fokuserar på globala samhällsutmaningar.

Energi
För omställning till hållbara energisystem och samsyn kring långsiktiga utmaningar.

Hälsa och teknik
Hållbara lösningar av stora hälsorelaterade samhällsutmaningar, i nära samarbete med sjukvården.

Informations- och kommunikationsteknik, digitalisering och AI
Siktar mot ett smartare och säkrare samhälle.
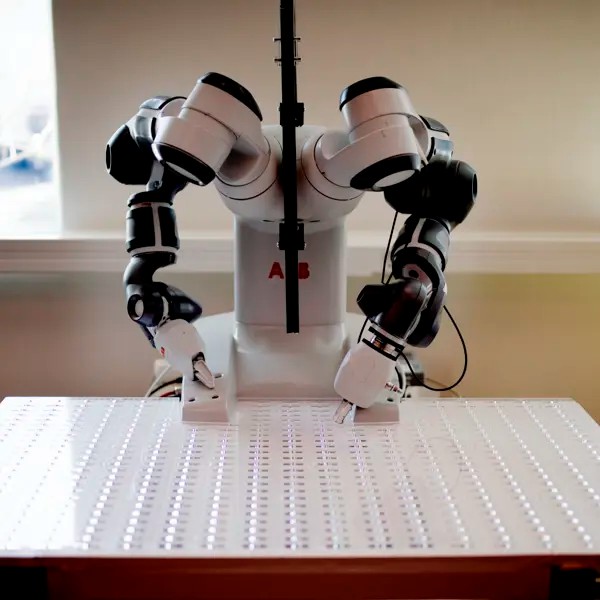
Industri och produktion
En hållbar industri genom omställning till cirkulär ekonomi, industriell digitalisering och användning av nya material.

Mark
Med en växande befolkning ökar behoven av välplanerade och välfungerande samhällen med tillgång till såväl rent vatten och sanitet, fler men också klimatanpassade bostäder och motståndskraftig infrastruktur för vatten, energi och transport såväl som ett hållbart jord- och skogsbruk.
Materialvetenskap
Vi möjliggör grön omställning genom excellent materialvetenskap inom energi, hälsa, konstruktion och transport.

Nano- och kvantvetenskap och teknologi
Forskning på de unika kemiska och fysiska fenomen som existerar i mycket små dimensioner, och på tillämpningar inom elektronik, bioteknik och energiteknik.

Ocean
Chalmers har en lång tradition av marin och maritim forskning och utbildning. Idag arbetar många av våra institutioner med frågor som rör havet och dess resurser, i linje med FN:s decennium för havsforskning för hållbar utveckling. Området Ocean innefattar olika aspekter av blå ekonomi, till exempel värdehöjning av marin råvara, havsplanering och riskbedömning av aktiviteter till havs.

Rymd
Hållbara lösningar inom rymdteknik för att möta samhällsutmaningar nu och i framtiden, inom och utanför vår planets gränser.

